
The web hosting industry, like any specialized industry, has its own unique set of terminology, definitions, and abbreviations.
This Hosting glossary contains some of the most common terms you are likely to need to know when managing your web hosting account.
A
Access Logs
What are Access Logs?
Access Logs are log files that record all requests to a web server.
They typically include information such as the IP address of the client making the request, the date and time of the request, and the outcome of the request, such as whether it was successful or returned an error.
Access logs are helpful for debugging, security, and traffic analysis. Web analytics tools also use them to track visitor behavior and generate statistics about website usage.
Account
What is an Account?
A user account created on a web hosting service allows users to access and manage their hosting services, such as setting up email accounts, creating databases, and installing software.
Active Directory
What is Active Directory?
Active Directory is a directory service that Microsoft developed for Windows domain networks. It stores information about a network’s resources and users and allows administrators to manage and secure their network.
Active Directory stores information in a hierarchical structure and enables centralized management of resources such as users, computers, and other devices. It allows for user authentication, authorization, and access control to the resources on a network.
It also provides a central point of administration for distributed networks, enabling administrators to manage and secure their network from a single location.
Add-on Domain
What is Add-on Domain?
An add-on domain is a secondary domain that is added to a primary domain. It allows hosting multiple domain names on the same hosting account, and each domain can have its own web content and email accounts.
An add-on domain is a separate website that can be accessed using a different domain name, but it shares the same hosting space and resources as the primary domain.
This feature allows users to add additional websites to their hosting account without purchasing further hosting plans or managing separate hosting accounts for each website.
AJAX (Asynchronous JavaScript and XML)
What is AJAX?
AJAX (Asynchronous JavaScript and XML) is used to create dynamic, interactive web pages by exchanging small amounts of data with the server behind the scenes.
AJAX allows web pages to update asynchronously by exchanging data with a web server in the background. This means that the browser doesn’t need to reload the entire page when new information is required, improving the user experience and making web pages faster and more responsive.
AJAX typically uses the XMLHttpRequest object to send and receive data to and from a server and JavaScript to manipulate the page on the client side.
AJAX combines various technologies like JavaScript, XML, HTML, and CSS. It allows for an improved web development experience for developers and a better end-user experience for the end users.
Analytics
What is Analytics?
Analytics is a tool used to measure and track website traffic and other metrics, such as the number of visitors, the pages they visit, and how long they stay on the site.
Analytics can provide valuable insights into a website’s performance and can be used to optimize its design and content.
Anonymous FTP
What is Anonymous FTP?
A type of FTP (File Transfer Protocol) connection allows users to connect to a server without providing a username or password. Anonymous FTP is typically used to provide public access to specific files or directories on a server.
Anti-DDoS (Anti-Distributed Denial of Service)
What is Anti-DDoS?
Anti-DDoS, short for Anti-Distributed Denial of Service, is a security feature that can protect a website from a DDoS (Distributed Denial of Service) attack.
DDoS attacks attempt to make a website unavailable by overwhelming the server with traffic from multiple sources. Anti-DDoS can help detect and block these attacks to keep a website available to legitimate users.
Apache
What is Apache?
Apache is an open-source HTTP (Hypertext Transfer Protocol) web server software, commonly used on Linux web servers. Apache is known for its flexibility, robustness, and security and it is widely used to host websites of all types and sizes.
Apache Modules
What are Apache Modules?
Apache Modules are add-ons for the Apache web server software that extend its functionality. They are used to add new features, optimize performance, or provide additional security.
Apache modules are usually written in the C programming language and are loaded dynamically by the Apache server at runtime. They can be installed and activated by the server administrator.
Some examples of common Apache modules are:
mod_rewrite: allows URLs to be written in a more user-friendly format.mod_ssl: provides SSL/TLS encryption for secure data transfermod_deflate: provides compression of web pages to reduce the bandwidth needed to transfer data
Some modules may come pre-installed by the Operating System.
API (Application Programming Interface)
What is API (Application Programming Interface)?
An API, or Application Programming Interface, is a set of rules and protocols for building and integrating software applications. It specifies how software components should interact, and APIs allow communication between different systems.
APIs can be used to access the functionality of an operating system, application, or web-based system. They enable developers to access the features or data of an application, operating system, or other services.
APIs are used in web development to allow for integration with other websites or to create custom web-based applications or mobile apps that communicate with a web service or back-end system.
Application Hosting
What is Application Hosting?
Application Hosting is a type of web hosting that specifically supports and runs certain applications, such as a CMS (Content Management System) or forum software.
This type of hosting is often tailored to the application’s specific requirements and may include additional security measures to ensure the application is running smoothly.
One of the most popular types of application hosting is WordPress hosting.
Application Server
What is Application Server?
An application server is a server that hosts, runs, and manages applications and services.
It acts as a middleware between the application and the database, and it abstracts the underlying complexity of the system, allowing for the development of simple, easy-to-use applications.
An application server provides a platform for applications to run, handles connections to the database, manages security, and provides many other services.
It also provides a runtime environment for the application, where the application logic can be executed.
Application servers can be used for a wide range of applications, including web-based, mobile, and enterprise applications.
ASN (Autonomous System Number)
What is ASN (Autonomous System Number)?
An Autonomous System Number (ASN) is a unique number assigned to identify an Autonomous System (AS) in the Internet’s globally unique routing system.
An AS refers to a collection of networks and routers under the control of one or more network operators that presents a common routing policy to the Internet.
ASNs are assigned by a regional internet registry (RIR) such as ARIN, RIPE, APNIC, LACNIC, or AfriNIC. They are used in the Border Gateway Protocol (BGP) routing protocol to identify the path that data packets take through the internet.
ASNs are essential for IP routing, ensuring that data packages are forwarded to the correct location.
ASP (Active Server Pages)
What is ASP (Active Server Pages)?
ASP (Active Server Pages) is a Microsoft technology that allows developers to create dynamic web pages using server-side scripting.
ASP enables developers to create web pages that can include a mix of server-side scripts and HTML, and it allows the code to be executed on the server before the page is sent to the client’s web browser. This means that the application logic can be executed on the server, and the results are then returned to the client’s web browser to be rendered.
ASP was one of the first web development technologies to allow for server-side scripting, and it has since been replaced by newer technologies such as ASP.NET, but it is still in use in some legacy applications.
AUP (Acceptable Use Policy)
What is AUP?
AUP (Acceptable Use Policy) is a policy that outlines the acceptable behavior of users of a web host’s services. This typically includes guidelines for using the hosting service for legal and appropriate purposes and can be used to restrict certain types of content or activity on the server.
Authentication
What is Authentication?
Authentication is the process of verifying the identity of a user or system. It is a fundamental security measure that ensures only authorized parties can access a system or network.
Authentication is typically achieved through a combination of a username and password. The system checks the credentials provided by the user against a database of valid credentials, and if the credentials match, the user is granted access.
There are different types of authentication mechanisms, such as multi-factor authentication (MFA), which combines multiple authentication methods such as passwords, security tokens, and biometric authentication, increasing the security of the authentication process.
Auto-scaling
What is Auto-scaling?
Auto-scaling is the process of automatically increasing or decreasing the capacity of a resource, such as a server, in response to changes in demand.
Auto-scaling is a feature of cloud computing platforms that enables users to automatically provision and de-provision resources, such as servers, based on the workload. It allows the system to automatically adjust the number of resources to match the demand, ensuring that the system is neither over- nor under-provisioned.
Auto-scaling can be used to scale resources up or down in response to changes in demand, such as increased website traffic. It can be used to manage costs by automatically de-provisioning resources when they are no longer needed. It can also be used for High availability and disaster recovery of systems.
Automatic Updates
What are Automatic Updates?
Automatic Updates are a feature of some web hosting services that automatically updates the software and security patches on the server without needing manual intervention. This helps keep the server secure and running the latest software versions.
A typical example is where hosting providers update your WordPress installation, including the application and plugins.
AWS (Amazon Web Services)
What is AWS (Amazon Web Services)?
AWS (Amazon Web Services) is a collection of remote computing services (also called web services) that make up a cloud computing platform offered by Amazon.com.
AWS provides a wide range of services, including storage, networking, database, analytics, application services, deployment, management, mobile, developer tools, tools for the Internet of Things (IoT), and more.
AWS is one of the most widely used and well-known cloud computing platforms, and it is used by small and large businesses and government and educational institutions.
AWStats
What is AWStats?
AWStats is a web log analyzer that generates statistics graphically from log files.
It can process log files from many different web servers, such as Apache, IIS, and WebStar. The tool provides advanced graphical reports on website visitors, including how many visitors, pages visited, files downloaded, and searches made.
Apache Web Server
What is an Apache Web Server?
Apache is the most widely used web server software to deliver web pages on the Internet. It is open-source software developed and maintained by the Apache Software Foundation.
Autoresponder
What is an Autoresponder?
An email Autoresponder enables you to automatically send responses to emails if you are unavailable for any reason. They are often used to set up away messages when you are on holiday.
Read more:
B
Backup
What is Backup?
A backup refers to creating a copy of data to protect against data loss in case of hardware failure, software corruption, or other unforeseen events.
Most hosting providers offer backups as a service. Backups are usually performed on a daily basis and are stored on the same server as the data being backed up. Backups can also be stored in an offsite location.
Some key features of backups are:
- Data Protection: Backups protect data from being lost due to hardware failure, software corruption, or other unforeseen events.
- Restoring Data: Backups allow you to restore data to its previous state in case of data loss.
- Versioning: Backups can keep multiple versions of the same data.
- Offsite Storage: Backups can be stored in an offsite location so that the data can still be recovered even in case of a disaster on-site.
It’s important to note that backups should be tested regularly to ensure they can be successfully restored in case of data loss.
Balancing (load)
What is load balancing?
Load balancing is the process of distributing incoming network traffic across multiple servers or resources to ensure that no single server or resource is overwhelmed by too much traffic.
The goal of load balancing is to ensure that all servers or resources are used efficiently and that no single server or resource is overwhelmed. This can be achieved by distributing the incoming traffic across multiple servers, using techniques such as round-robin, least connections, or IP hash.
There are two types of load balancing: hardware-based and software-based. Hardware-based load balancers use specialized hardware appliances while software-based load balancers are implemented using software running on general-purpose hardware.
Load balancing is an essential component of a high-availability infrastructure and it is critical for ensuring that web applications and services remain available and responsive, even under heavy load.
Bandwidth (limit)
What is a Bandwidth limit?
A bandwidth limit is the maximum amount of data transmitted over a network connection in a certain amount of time.
Bandwidth limits are often used to regulate the amount of data transferred by different types of network connections, such as broadband and dial-up connections, or to manage the amount of data transmitted over a shared connection.
A common use of bandwidth limits is in web hosting, where customers are allotted a certain amount per month. If a customer exceeds their bandwidth limit, they may be charged an overage fee or have their service temporarily suspended.
It is essential for website owners, developers, and providers to monitor the bandwidth usage of their servers, application, and website to ensure that they are not exceeding the limits and causing additional charges or service interruptions.
Base64
What is Base64?
Base64 is a group of binary-to-text encoding schemes representing binary data in an ASCII string format by translating it into a radix-64 representation.
Base64 represents data in a way that can be included in a plain text format, such as an email or an HTML file.
It is helpful when you want to send or store binary data through a mechanism that only handles text.
Some of the key features of Base64 are:
- It’s a simple way to encode binary data into ASCII text
- It’s commonly used to embed data, such as image files, in HTML, CSS, JavaScript, or anything that is part of text-based formats
- It can be used to encode login credentials to be passed in an HTTP request
- It is often used to encode and decode user data, like passwords, which are stored in a database.
It’s important to note that Base64 is not a form of encryption. It’s intended to encode data, not protect it from prying eyes.
Bcrypt
What is Bcrypt?
Bcrypt is a password-hashing algorithm based on the Blowfish encryption algorithm. It is used to securely store user passwords in a way that makes them difficult to crack.
Bcrypt uses a unique salt for each password and applies a cost factor (work factor) to increase the computational cost of hashing passwords, making it resistant to brute-force attacks.
Bcrypt has some key features, such as:
- Secure: Bcrypt was designed to be more secure than other password-hashing algorithms.
- Slow: Bcrypt is intentionally slow to slow down brute-force attacks.
- Adaptable: Bcrypt can be configured to increase the computational cost of generating a password hash.
- Portable: Bcrypt is implemented in various languages, including C, C++, Go, Java, JavaScript, PHP, and Python.
It’s important to note that Bcrypt is a one-way function, meaning that once a password is hashed, it cannot be unencrypted. This is why storing bcrypt hashed passwords in a database is safe.
Bitrate
What is Bitrate?
Bitrate is the number of bits conveyed or processed per unit of time. It is typically measured in bits per second (bps) or bytes per second (Bps).
Bitrate is a measure of the amount of data that is transmitted or processed over a network connection or storage media.
Bitrate is commonly used when talking about:
- Audio/Video codecs: Bitrate represents the number of bits per second used to encode a video or audio stream. A higher bitrate means a higher quality video and a larger file size.
- Streaming: The bitrate is used to measure the quality of a video stream. A higher bitrate means better quality video, but it also means a higher demand for internet bandwidth.
- Networking: Bitrate measures the amount of data transmitted over a network. It is often measured in terms of bits per second.
It’s important to note that when talking about video and audio, a high bitrate doesn’t always mean high quality. Other factors, such as resolution and color depth, can also play an essential role in determining the overall quality of the video or audio.
Bandwidth
What is Bandwidth?
Bandwidth is the amount of data transferred to and from your web server. Hosting companies will either set a monthly bandwidth limit or make it unlimited (subject to fair use, so it’s not unlimited).
Blog
What is a Blog?
A blog is a website featuring a list of articles, journals, or other informational posts in date order, with the newest at the top. In the beginning, most blogs were written by one person. Today, many blogs are written by whole teams, usually based around a single topic or theme, such as technology or politics.
The most popular blogging platform is WordPress.
C
Cache
What is Cache?
Cache refers to a temporary storage area where frequently accessed data can be quickly retrieved.
There are several types of caches that can be used in web hosting, including:
- Browser cache: Caches content on a user’s computer so that it can be quickly loaded the next time the user visits the same website.
- Server cache: Caches content on the server so that it can be quickly delivered to the user without having to be re-generated.
- Content Delivery Network (CDN) cache: Caches content on a network of servers distributed worldwide so that it can be quickly delivered to the user, regardless of location.
Caching can significantly improve a website’s performance and speed by reducing the time and resources required to generate and deliver content to the user.
It’s important to note that caching can also cause issues if the cached content is outdated or if the cache is not correctly managed.
CGI-bin
What is CGI-bin?
The CGI-bin is a directory on a web server that is used to store Common Gateway Interface (CGI) scripts.
CGI is a way to execute scripts on a web server. It allows dynamic content to be generated by a web server. These scripts can be written in various programming languages, such as Perl, Python, and Shell.
The CGI-bin directory is typically located in the web root directory of the server and is used to store the CGI scripts executed by the web server.
It’s important to note that CGI-bin is a legacy feature and is not used as much today as it was in the past. Many web servers support other ways to execute scripts like PHP, Ruby, or Node.js.
Cloud Hosting
What is Cloud Hosting?
Cloud hosting uses a network of remote servers, often located in different parts of the world, to store, manage, and process data.
Cloud hosting provides several benefits over traditional web hosting, including:
- Scalability: Cloud hosting allows resources to be easily added or removed as needed so that websites can handle fluctuations in traffic.
- Reliability: Cloud hosting uses multiple servers, so if one fails, the others can take over without interruption.
- Cost-effectiveness: Cloud hosting allows users to pay only for the resources they use rather than having to pay for dedicated hardware.
Content Delivery Network (CDN)
What is Content Delivery Network (CDN)?
A Content Delivery Network (CDN) is a network of servers distributed worldwide to deliver content to users based on their geographic location.
CDNs work by caching content on a network of servers so that when a user requests a piece of content, they are delivered the cached version from the server closest to them. This helps reduce the time and resources required to provide content to the user.
CDNs are commonly used to deliver images, videos, and other large files, as well as to improve the performance and security of websites.
Some key features of CDNs are:
- Improved Performance: CDNs can significantly improve a website’s performance by reducing the time and resources required to deliver content to the user.
- Improved Security: CDNs can also improve the security of a website by providing features such as DDoS protection and SSL offloading.
- Global Coverage: CDNs have servers distributed around the world, allowing for faster content delivery to users regardless of location.
It’s important to note that CDN services can vary significantly in terms of features, pricing, and quality, and it is essential to evaluate different options before choosing a CDN provider.
Control Panel
What is Control Panel?
A control panel is a web-based interface that allows users to manage various aspects of their website, such as email accounts, databases, and file management.
Web hosting companies use a control panel to provide their customers with a way to manage their websites. Some of the features that it might include are:
- Email management: creating, managing, and forwarding email accounts
- File management: uploading, downloading, and managing files on the web server
- Database management: creating, managing, and backing up databases
- Software installation: installing popular software, such as WordPress, through a simple interface
There are many different control panels available. Some of the most popular ones are cPanel, DirectAdmin, and Plesk.
It’s important to note that control panels can vary significantly in terms of features and ease of use. It is essential to evaluate different options before choosing a control panel.
cPanel
What is cPanel?
cPanel is a web-based control panel for managing web hosting. It allows users to manage various aspects of their website, such as email accounts, databases, and file management, through a user-friendly interface.
cPanel is commonly used by web hosting companies to provide their customers with a way to manage their websites. Some of its features include:
- Email management: cPanel allows users to create, manage, and forward email accounts.
- File management: cPanel allows users to upload, download, and manage files on their web server.
- Database management: cPanel allows users to create, manage, and backup databases.
- Software installation: cPanel makes it easy to install popular software, such as WordPress, through a simple interface.
It’s important to note that cPanel is third-party software and is not included with all web hosting plans.
You can view a screenshot of the cPanel admin area below:

Read more:
Cron
What is Cron?
Cron is a time-based job scheduler in Unix-like operating systems. Cron enables users to schedule jobs (commands or scripts) to run automatically at specified intervals.
Cron uses a configuration file called crontab, which contains a list of commands to be executed and the schedule on which they are to be performed.
Cron is commonly used to automate repetitive tasks such as:
- Database backups
- Sending emails
- Updating data
- Clearing cache
It’s important to note that Cron is a command-line tool and requires some technical knowledge to set up and use.
Catch-all Email Address
What is a Catch-all Email Address?
A catch-all email address is a default address designated to receive any emails not sent to a valid email address on your domain. Some control panels, such as cPanel, refer to this as the “default address.”
You can only set up one catch-all email address per domain. If you wish for multiple people to receive emails from this address, you can always set up email forwarding.
Read more:
CMS
What is a CMS?
CMS is short for Content Management System and is software that lets users create, manage, and modify content on their website via a simple graphical interface. The most popular CMS is WordPress. Most web hosts provide a one-click install from the control panel many different types of CMS.
D
Database
What is a Database?
A database is a collection of data organized to allow for efficient storage, retrieval, and manipulation of data.
Databases are commonly used to store and manage large amounts of data and are essential to many web applications. There are many different types of databases, such as relational databases, NoSQL databases, and in-memory databases, each with its strengths and weaknesses.
Some typical features of databases include:
- Tables: A table is a collection of data organized into rows and columns.
- Indexes: An index is a data structure that allows for faster searching of data in a table.
- Queries: A query is a database’s command to retrieve or manipulate data.
It’s important to note that databases require a certain level of technical knowledge to set up and manage, and it is vital to choose the right type of database for a specific use case.
Database Backup
What is Database Backup?
A database backup is a copy of a database made for recovery in case of data loss.
Database backups are essential to maintaining data integrity and availability and should be a regular part of any database management strategy.
There are many different methods for creating backups, such as:
- Full backups: A full backup creates a copy of the entire database
- Incremental backups: An incremental backup creates a copy of only the data that has changed since the last backup
- Differential backups: A differential backup creates a copy of all the data that has changed since the last full backup
It’s important to note that Database backups should be stored in a secure location and regularly tested to ensure that they can be used to restore the database in case of data loss.
DDoS
What is DDoS?
DDoS (Distributed Denial of Service) is a type of cyber attack in which many computers, often compromised through malware or botnets, are used to flood a website with traffic to make it unavailable to legitimate users.
DDoS attacks can be launched using various techniques, such as flooding a website with traffic from multiple sources, overwhelming the server’s resources, and making it unavailable.
DDoS attacks can significantly impact a website’s availability and can cause financial losses for the targeted organization.
Some common techniques used in DDoS attacks are:
- Amplification attacks
- Application-layer attacks
- Network-layer attacks
- TCP/UDP floods
It’s important to note that DDoS attacks can be mitigated using various techniques, such as a Content Delivery Network (CDN) or a DDoS protection service such as CloudFlare. It is essential to have a plan in place to deal with DDoS attacks.
Dedicated Hosting
What is Dedicated Hosting?
Dedicated hosting is a web hosting service in which a single customer rents an entire physical server from a web hosting provider.
Dedicated hosting allows complete control over the server, including the operating system, hardware, and software. This makes it ideal for websites with high traffic, high security, or special software requirements.
In dedicated hosting, the client has full access and control over the server and is responsible for its maintenance and troubleshooting. The client can also configure the server to their specific needs and preferences.
Some benefits of dedicated hosting include the following:
- Increased security
- Better performance
- More control and flexibility
- Scalability
It’s important to note that dedicated hosting can be more expensive than other types of hosting, such as shared hosting and VPS hosting, and requires a certain level of technical knowledge to set up and manage, although fully managed solutions are available.
Dedicated IP
What is a Dedicated IP?
A dedicated IP address (Internet Protocol address) is a unique internet address assigned to a single domain. It is not shared by multiple domains.
There are a few minor benefits to using a dedicated IP address. These include visiting your website via the IP address, accessing your FTP address if your Domain Name is still propagating, and helping prevent your IP from getting blacklisted. For most webmasters, a shared IP is perfectly fine.
A dedicated IP used to be a requirement to install an SSL certificate, but most hosting providers now support SNI (Server Name Indication). SNI allows multiple SSL certificates on a single IP address.
DNS
What is DNS?
DNS (Domain Name System) is a system that translates human-friendly domain names, such as www.example.com, into the IP addresses that are used by computers to identify each other on the internet.
DNS is an essential part of the internet infrastructure, as it allows users to easily remember and access websites rather than having to remember the numerical IP addresses.
DNS comprises a hierarchical system of servers, with the root servers at the top of the hierarchy and the domain name registrars and name servers at the bottom.
DNS functions by:
- Resolving domain names to IP addresses
- Caching resolved domain names for a period of time
- Providing redundancy and distributed load-sharing
It’s important to note that DNS can be a complex system, and there are several ways to configure DNS. Understanding the basics of DNS is essential to manage a website effectively.
Read more:
Domain Name
What is Domain Name?
A domain name is a human-friendly address representing a specific IP address on the internet. They are used to identify and locate websites, emails, and other resources on the internet.
A domain name comprises the top-level domain (TLD) and the second-level domain (SLD). The TLD is the domain name extension, such as .com, .net, .org, etc., and the SLD is the unique name registered, such as Google, Amazon, Facebook, etc.
For example, in the domain name “www.google.com”, “google” is the second-level domain, and “.com” is the top-level domain.
Domain names are registered with registrars, organizations accredited by the Internet Corporation for Assigned Names and Numbers (ICANN), to manage the registration of domain names.
It’s important to note that domain names are unique; once registered, they cannot be registered by anyone else. Also, domain names can be purchased for a specified period, usually between 1 and 10 years.
Datacenter
What is a Datacenter?
A datacenter is a secure facility that houses web hosting servers. It includes physical servers and other components such as firewalls, switches, and routers to ensure reliable and resilient external network connectivity. Web hosts will usually have servers in multiple datacenter locations so that you can choose a server nearer your or your users’ location for decreased network latency.
Disk Space
What is Disk Space?
Disk space is the amount of storage space available in your hosting plan. Disk space will be used for your website files and databases, as well as emails and cached website files.
There are different types of disk space, including SATA (traditional) and SSD, and these may be arranged in various configurations. For example, RAID 1 mirrors multiple disks for redundancy, RAID 0 creates an array for faster performance, and RAID 10 combines both methods. RAID 10 storage is the best.
E
Elastic Compute Cloud (EC2)
What is Elastic Compute Cloud (EC2)?
Elastic Compute Cloud (EC2) is an Amazon Web Services (AWS) web service. It allows individuals and organizations to rent virtual computers, known as instances, to run their own applications.
EC2 instances are flexible and customizable, and they can be launched and terminated on demand, making it easy to scale up or down as needed. Depending on the application’s needs, they can also be configured with various combinations of CPU, memory, and storage.
EC2 instances run on top of Amazon’s virtualized infrastructure, providing a high availability and reliability level. They can also be configured to run in different regions and availability zones, providing data sovereignty, compliance, and disaster recovery options.
It’s important to note that while EC2 is a service provided by Amazon, other providers, such as Microsoft Azure, Google Cloud Platform, and Digital Ocean, also offer similar services like Virtual Machines and Containers.
Email hosting
What is Email hosting?
Email hosting is a service that allows individuals and organizations to create and manage email accounts using their own domain name. Web hosting companies typically provide this service, which is often included as part of a web hosting package.
With email hosting, users can create email addresses that use their own domain name, such as “[email protected]”, rather than a generic email address provided by a free email service. This can give a more professional image, and it also allows for better organization of emails.
The email hosting service typically includes a web-based interface, allowing users to access their email from anywhere. It also often has features such as email forwarding, auto-responders, and email filtering.
Error log
What is an Error log?
An error log is a file that records a web server’s error messages and other diagnostic information. These logs are typically stored on the server and can be used to troubleshoot problems with the server or with specific web applications.
Error logs typically include information such as the date and time of the error, the type of error (e.g., 404 error indicating a page not found), and the file or script that caused the error. They also often include a message describing the error and, in some cases, a stack trace that can be used to identify the specific line of code that caused the error.
Error logs are essential for identifying and troubleshooting problems with a web server or web application. They can also monitor the server for potential security issues, such as attempted hacking.
It is important to regularly check the error logs and address any errors or warnings which may have occurred.
Expires header
What is Expires header?
The Expires header is an HTTP (Hypertext Transfer Protocol) header field that indicates when a particular resource expires. The value of the Expires header is a date and time, representing the point at which the resource is considered stale and should no longer be cached by the client.
When a client (such as a web browser) requests a resource from a server, the server can include an Expires header in the response and the resource itself. The client can then cache the resource and use it for subsequent requests rather than requesting the resource again from the server until the resource expires.
By setting an appropriate value for the Expires header, web developers can improve the performance of their websites by reducing the number of requests made to the server. This is particularly useful for infrequently changing resources, such as images, CSS files, and JavaScript files.
It’s important to note that the Expires header is just one of several mechanisms that can be used to control caching. Different types of resources may require different caching strategies. Other mechanisms include the Cache-Control header and the max-age directive.
Email Spam
What is Email Spam?
Email spam, otherwise known as junk mail, is the unsolicited emails sent out on mass to email recipients. It is usually sent out by an automated system with commercial or nefarious intent.
Error Page
What is an Error Page?
An error page with a status code is displayed when there is an error with the page you are trying to access. Status codes are divided into classes and subclasses, with the error codes starting with 4xx and 5xx. These are as follows:
- 4xx: client errors - the page can’t be found or reached.
- 5xx: server errors - the request can not be completed.
F
File Transfer Protocol (FTP)
What is File Transfer Protocol (FTP)?
File Transfer Protocol (FTP) is a standard network protocol that transfers files between computers on a private or public network. FTP enables the transfer of files between a local host and a remote host or between two remote hosts.
FTP is based on a client-server architecture, where an FTP client establishes a connection to an FTP server, sends commands, and receives responses to transfer files.
Modern operating systems widely support FTP, including Windows, Linux, and macOS. It can also be used via the command-line or a graphical user interface (GUI) through various software such as FileZilla, CuteFTP, and WinSCP.
Firewall
What is a Firewall?
A firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on a set of security rules and policies. The primary purpose of a firewall is to prevent unauthorized access to or from a private network.
Firewalls can be implemented in hardware, software, or a combination of both.
Fantastico
What is Fantastico?
Fantastico is an auto-installer allowing for the easy installation of hundreds of web applications, including WordPress. It is popular with shared web hosting providers who offer it to their customers via the control panel.
File Permission
What is a File Permission?
File permissions are the rights given to a user to view, edit, or have complete access to files. File permissions can sometimes cause issues with WordPress or other software if not correctly configured. Although if you install software through an auto-installer, you should rarely have a problem with file permissions.
H
.htaccess
What is .htaccess?
The .htaccess file is a configuration file that allows you to control how your webserver deals with specific requests. It is used on Apache web servers, but not NGINX servers. You can use .htaccess files to specify error documents, set passwords to directories or your entire site, blacklist or whitelist IPs, and add redirects. WordPress even has a default .htaccess file configuration.
I
IMAP
What is IMAP?
IMAP is the acronym for Internet Message Access Protocol. IMAP is a protocol used for the processing of the transfer of emails between an email server and email client. All changes made with the IMAP protocol will be mirrored to your email server. IMAP won’t delete the email from the server after downloading it. It will keep any replies you make, read status, and record all other actions.
You can see the IMAP retrieval process in the following diagram:
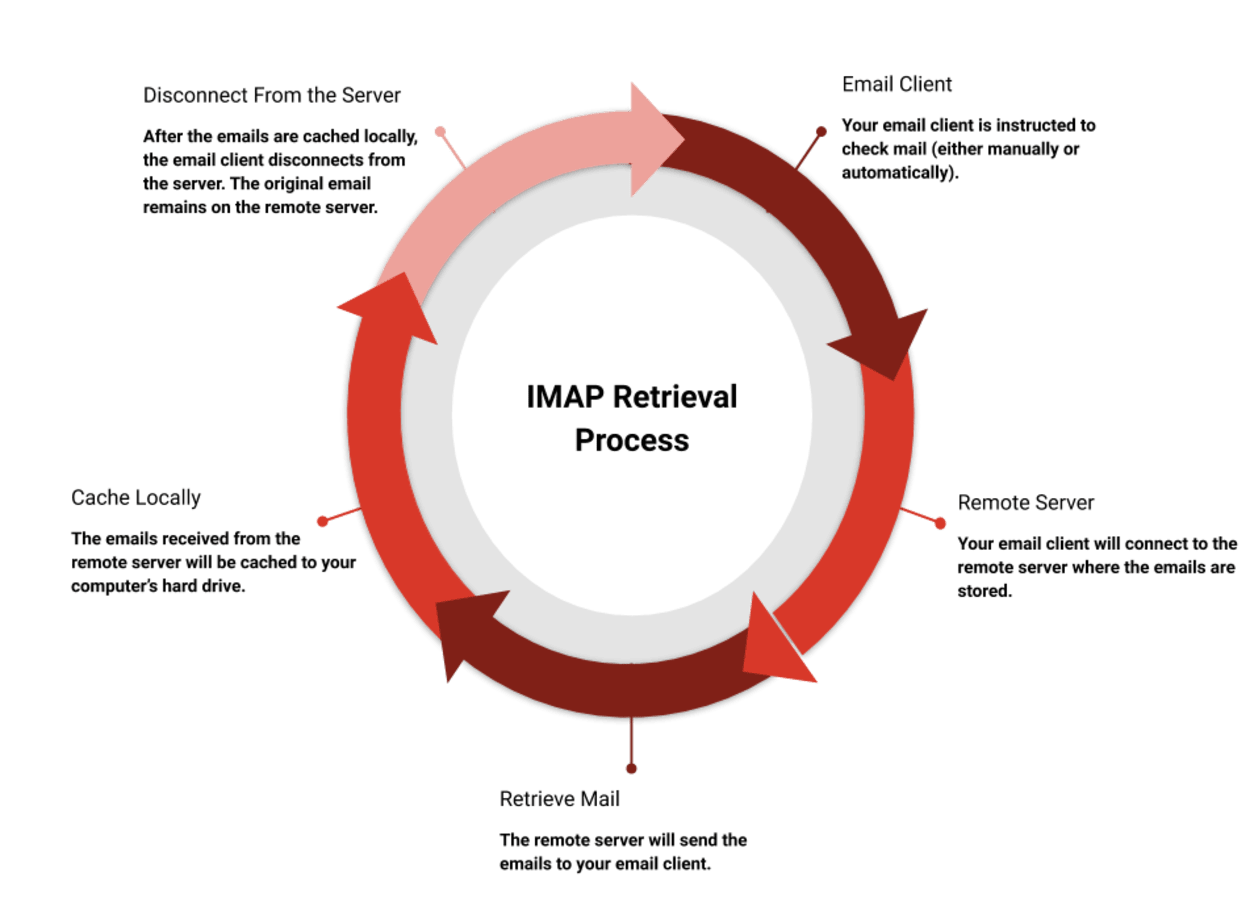
IMAP differs from POP 3, which deletes mail from the server after download and does not mirror actions taken in your email client.
See also:
Read more:
L
Linux Server
What is a Linux Server?
A Linux server is a server powered by the Linux Operating system. It is open-source and the most popular operating system among web hosting providers. If you have a WordPress blog or simple website, then you should choose Linux.
M
Malware
What is Malware?
Malware, short for malicious software, is a general term to describe viruses, worms, trojans, and other harmful programs used to infect, take over, or otherwise harm your website or server software.
MX Record
What is an MX Record?
An MX record is short for Mail Exchange Record. An MX record forms part of your DNS records is used to designate which mail servers are to be used to accept and send emails on your domain.
If your domain is registered with your hosting provider, this should be set up automatically. Otherwise, you will need to manually add your MX record with your domain registrar or third-party DNS provider.
MySQL
What is MySQL?
MySQL is an open-source relational database management system that uses a Structured Query Language (SQL). It is the most popular database management system and used in many software applications, such as WordPress.
O
Operating System
What is an Operating System?
The Operating System, or OS for short, is the software that supports the essential functions of the webserver. Most hosting providers offer Linux operating system, with many of those (but not all) also offering the Windows operating system. Unless you have a specific reason to choose Windows (for example, MS-SQL databases or ASP.NET), you should choose Linux. Linux works well for most purposes, including WordPress.
P
Parked Domain
What is a Parked Domain?
A parked domain is a domain name that you own that does not point to a hosting, email service or anything else. Like a parked car, a parked domain is not being used and does nothing.
Unless you setup a redirect or alias for your parked domain, many domain registrars will display a default parking page. For example, Namecheap displays the following:

phpMyAdmin
What is phpMyAdmin?
phpMyAdmin is one of the most popular database management tools for MySQL. It is a free tool provided in most control panels, such as cPanel or Plesk. It allows you to create, alter, drop, delete, import, and export MySQL tables, as well as run queries and other commands.
Plesk
What is Plesk?
Plesk is a popular control panel used for managing web hosting. It features a user-friendly graphical interface, so you do not need any technical knowledge to manage your hosting.
Because it is easy to use, it is very popular with many web hosting providers. You can manage your files, email addresses, domains, backups, and databases through the Plesk control panel. Optional extras include a WordPress toolkit, including staging, security, backups, SEO optimization options, and more.
You can view a screenshot of the Plesk admin area below:

POP 3
What is POP 3?
POP is the acronym for Post Office Protocol. POP 3 is a protocol created in 1988 that is used to process the transfer of emails between an email server and email client. POP 3 will download any message from your mail server, but any changes you make to the downloaded message will only exist on your local computer. The default behavior of POP 3 is to delete the messages from the server once downloaded. If you or anyone else accesses your emails from another computer or device will not know what you have done or even know the emails you accessed exist.
You can see the IMAP retrieval process in the following diagram:
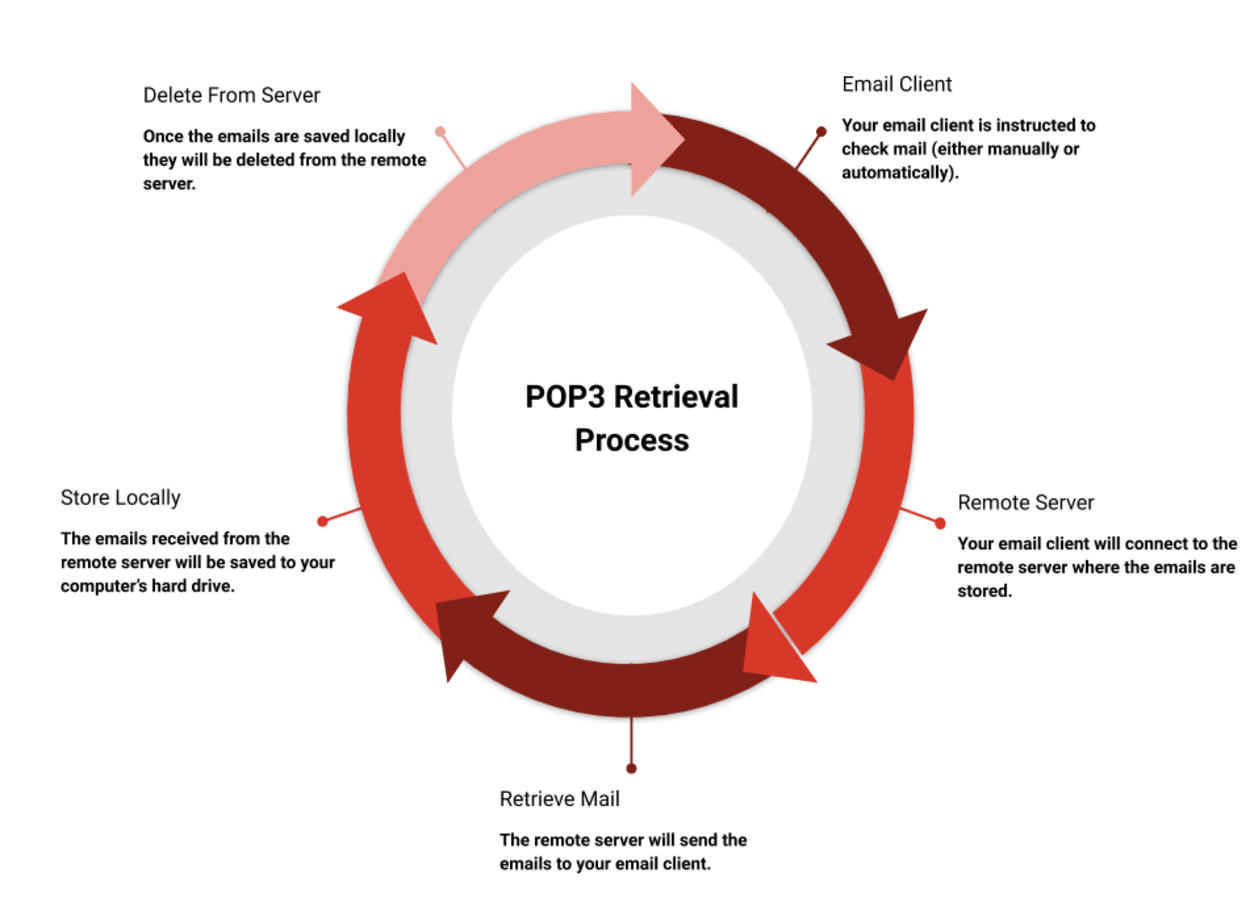
POP 3 differs from IMAP, as IMAP won’t delete the email from the server after downloading it. It will also keep any replies you make, read status, and record all other actions.
See also:
Read more:
R
Reseller Hosting
What is Reseller Hosting?
Reseller hosting is where the user can resell web hosting accounts to their customers. These accounts are popular with developers who host client sites or people looking to start a web hosting business. The reseller can sell them for profit.
S
Shared Hosting
What is Shared Hosting?
Shared hosting is a type of web hosting where multiple users share a single server’s resources, although some hosting providers now use a hyperscale cloud such as Google or Amazon. Shared hosting is suitable for those with low-traffic websites.
SLA
What is SLA?
SLA is short for Service Level Agreement. An SLA is an agreement you will have with your hosting company. It sets out the rules related to the service, rights, responsibilities, uptime guarantee (along with exclusions), and other conditions for your hosting product.
Softaculous
What is Softaculous?
Softaculous is an auto-installer allowing for the easy installation of up to 421 various web applications, including WordPress. It is popular with shared web hosting providers who offer it to their customers via the control panel.
Spam Filter
What is a Spam Filter?
A Spam Filter is a filter you can apply to emails to help identify spam. These can take the form of simple keyword-based filters, or more sophisticated systems such as SpamAssassin that use a variety of different detection methods, such as whitelists, DNS-based spam detection, sender reputation systems, and more.
SSH
What is SSH?
SSH, also known as Secure Socket Shell, is a network protocol that enables remote control of your server’s operating system. The communication between your computer and the remote server is encrypted.
SSL
What is SSL?
SSL stands for Secure Socket Layer. It is a means of encryption used to make the traffic to and from a website secure and allow a website to use the HTTPS prefix. Utilizing an SSL certificate is essential for security and because it is a Google Ranking Factor.
U
Uptime
What is Uptime?
Uptime is the amount of time your website or server is working correctly without interruption. Most hosting providers advertise their uptime as a percentage and supported by a guarantee.
See also:
Uptime Guarantee
What is an Uptime Guarantee?
An uptime guarantee is the level of uptime provided for your website as part of the web host’s service level agreement. The level of uptime is usually guaranteed for between 99% and 99.9%, with refunds paid for any breach. The amount of compensation paid is abysmal, so these guarantees are not worth much.
Read more:
See also:
V
VPS Hosting
What is VPS Hosting?
VPS hosting is short for Virtual Private Server. A VPS is a single server that uses virtualization technology to partition it into multiple sections, with each acting as its own web server. The VPS is usually more powerful than shared hosting, and the resources will often be shared between fewer users. They are generally seen as a stepping stone between shared hosting and dedicated hosting.
W
Web Server
What is a Web Server?
A Web Server is a server that runs software that stores and delivers content for a website in response to an HTTP request. While Apache is the most common web server software, others such as NGINX and LiteSpeed are also popular.
Webmail
What is Webmail?
Webmail is when you can access your emails directly via the web browser without the need to separate email software. Gmail and Hotmail are prime examples, although cPanel and Plesk come with free webmail software such as Horde and Roundcube. Webhosting companies also usually offer professional email services that you can access via webmail as well.
Read more:
Windows Server
What is a Windows Server?
A Windows server is powered by the Windows operating system. If you need ASP.Net or MS-SQL databases, you should opt for Windows hosting.
WordPress Hosting
What is WordPress Hosting?
WordPress hosting is hosting that has been optimized for WordPress. It often includes optimized hosting, including caching, extra security, site staging, and is usually managed. By managed, we mean that they may automatically update your WordPress plugins and core, provide backups, malware scanning, and more specialized support.